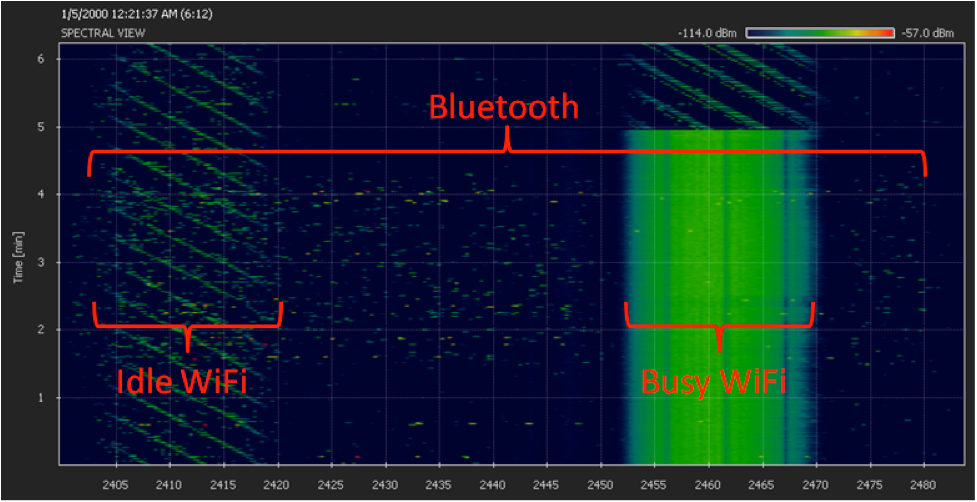
Kali Linux Advanced Wireless Penetration Testing: Bluesmack – Bluetooth DoS Script|packtpub.com - YouTube

Buy Kali Linux Wireless Penetration Testing Cookbook: Identify and assess vulnerabilities present in your wireless network, Wi-Fi, and Bluetooth enabled devices to improve your wireless security Online at Lowest Price in Ubuy

Hacking a Bluetooth Smart Lock. IoT Series — How to properly conduct… | by Theodoros Danos | InfoSec Write-ups